Securing RPL Using Network Coding: The Chained Secure Mode (CSM)
Considered the preferred routing protocol for many Internet of Things (IoT) networks, the routing protocol for low power and lossy networks (RPL) incorporates three security modes to protect the integrity and confidentiality of the routing process: 1) the unsecured mode (UM); 2) preinstalled secure mode (PSM); and 3) the authenticated secure mode (ASM). Both PSM and ASM were originally designed to protect against external routing attacks, in addition to some replay attacks (through an optional replay protection mechanism). However, recent research showed that RPL, even when it operates in PSM, is still vulnerable to many routing attacks, both internal and external. In this article, a novel secure mode for RPL, the chained secure mode (CSM), is proposed using the concept of intraflow network coding (NC). The CSM is designed to enhance RPL’s resiliency and mitigation capability against replay attacks. In addition, CSM allows the integration with external security measures such as intrusion detection systems (IDSs). An evaluation of the proposed CSM, from a security and performance point of view, was conducted and compared against RPL in UM and PSM (with and without the optional replay protection) under several routing attacks: the neighbor attack (NA), wormhole (WH), and CloneID attack (CA), using average packet delivery rate (PDR), end-to-end (E2E) latency, and power consumption as metrics. It showed that CSM has better performance and more enhanced security than both the UMandPSMwiththereplay protection while mitigating both the NA and WH attacks and significantly reducing the effect of the CA in the investigated scenarios.
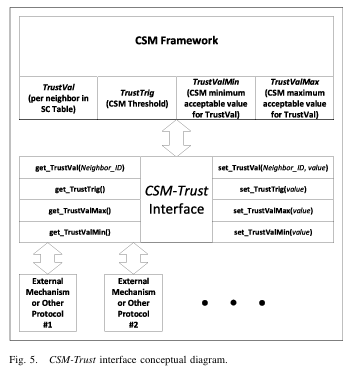
Raoof, C. -H. Lung and A. Matrawy, “Securing RPL Using Network Coding: The Chained Secure Mode (CSM),” in IEEE Internet of Things Journal, vol. 9, no. 7, pp. 4888-4898, 1 April 1, 2022, doi: 10.1109/JIOT.2021.3109109.1
Enhancing Routing Security in IoT: Performance Evaluation of RPL Secure Mode under Attacks
As the routing protocol for low power and lossy networks (RPL)s became the standard for routing in the Internet of Things (IoT) networks, many researchers had investigated the security aspects of this protocol. However, no work (to the best of our knowledge) has investigated the use of the security mechanisms included in RPL’s standard, mainly because there was no implementation for these features in any Internet of Things (IoT) operating systems yet. A partial implementation of RPL’s security mechanisms was presented recently for the Contiki operating system (by Perazzo et al.), which provided us with an opportunity to examine RPL’s security mechanisms. In this article, we investigate the effects and challenges of using RPL’s security mechanisms under common routing attacks. First, a comparison of RPL’s performance, with and without its security mechanisms, under four routing attacks [Blackhole, Selective-Forward (SF), Neighbor, and Wormhole (WH) attacks] is conducted using several metrics (e.g., average data packet delivery rate, average data packet latency, average power consumption, etc.). This comparison is performed using two commonly used radio duty cycle protocols. Second, and based on the observations from this comparison, we propose two techniques that could reduce the effects of such attacks without having added security mechanisms for RPL. An evaluation of these techniques shows improved performance of RPL under the investigated attacks, except for the WH.
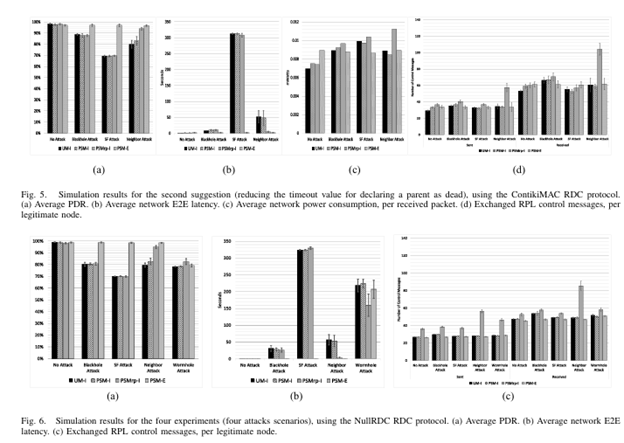
Ahmed Raoof, Ashraf Matrawy, and Chung-Horng Lung, “Enhancing Routing Security in IoT: Performance Evaluation of RPL Secure Mode under Attacks,” IEEE Internet of Things Journal (Early Access), September 2020.
Routing Attacks and Mitigation Methods for RPL-Based Internet of Things
The recent bloom of the Internet of Things (IoT) and its prevalence in many security-sensitive environments made the security of these networks a crucial requirement. Routing in many of IoT networks has been performed using the routing protocol for low power and lossy networks (RPL), due to its energy-efficient mechanisms, secure modes availability, and its adaptivity to work in various environments; hence, RPL security has been the focus of many researchers. This paper presents a comprehensive study of RPL, its known attacks, and the mitigation methods proposed to counter these attacks. We conducted a detailed review of the RPL standard, including a recently proposed modification. Also, we investigated all recently published attacks on RPL and their mitigation methods through the literature. Based on this investigation, and to the best of our knowledge, we introduced a first-of-its-kind classification scheme for the mitigation methods that is based on the techniques used for the mitigation. Furthermore, we thoroughly discussed RPL-based intrusion detection systems (IDSs) and their classifications, highlighting the most recently proposed IDSs.
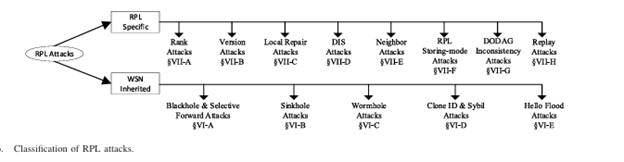
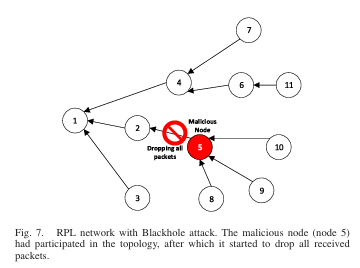
Ahmed Raoof, Ashraf Matrawy, and Chung-Horng Lung, “Routing Attacks and Mitigation Methods for RPL-Based Internet of Things,” IEEE Communications Surveys and Tutorials, (Early Access), December 2019.
On the Impact of the RPL Decreased Rank Attack on 6TiSCH Networks.
The 6TiSCH protocol stack was designed to provide a reliable and time-bound multi-hop routing solution for the Industrial Internet of Things (IIoT), integrating the IPv6 Routing Protocol for Low Power and Lossy Networks (RPL) and Time Slotted Channel Hopping (TSCH) protocols seamlessly. However, deviations from standard procedures by malicious nodes can severely affect network formation and operations, resulting in degraded performance. This study investigates the impact of the decreased rank attack (DRA) on RPL within the 6TiSCH network, examining its effects on network operations and performance. Experimental evaluation reveals that DRA can lead to an average delay of 21.4% in network formation and run time disruptions, thereby affecting the 6TiSCH synchronization process. Consequently, node departures from the network and subsequent rejoining to maintain the topology increase by an average of 60.71%. To deal with this disruption, the nodes need to send more keep-alive and RPL messages, resulting in an average increase of 69.70% and 20.08%, respectively, leading to a 49. 9% increase in energy depletion. Furthermore, the DRA reduces the packet delivery ratio and increases the average end-to-end packet delay by averages of 5.13% and 20%, respectively. However, it is important to note that the impact of the attack can vary significantly depending on the specific configurations and setups used, such as network topology, network size, attacker position, neighboring density, and RPL/TSCH parameter settings.
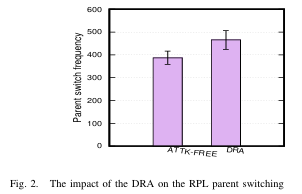
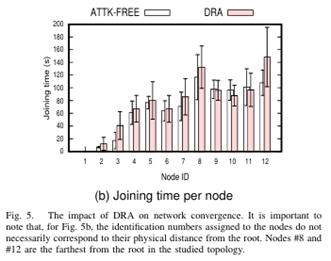
Mohammed Mahyoub, Sazzad Hossain, and Ashraf Matrawy (2024). On the Impact of the RPL Decreased Rank Attack on 6TiSCH Networks. Accepted at (2024 20th International Conference on the Design of Reliable Communication Networks (DRCN))
Integrating 6LoWPAN Security with RPL Using the Chained Secure Mode Framework”, The 14th IEEE International Conference on Internet of Things, 2021.
The IPv6 over Low-powered Wireless Personal Area Network (6LoWPAN) protocol was introduced to allow the transmission of Internet Protocol version 6 (IPv6) packets using the smaller-size frames of the IEEE 802.15.4 standard, which is used in many Internet of Things (IoT) networks. The primary duty of the 6LoWPAN protocol is packet fragmentation and reassembly. However, the protocol’s standard currently does not include any security measures, not even authenticating the fragments’ immediate sender. This lack of immediate-sender authentication opens the door for adversaries to launch several attacks on the fragmentation process, such as the buffer-reservation attacks that lead to a Denial of Service (DoS) attack and resource exhaustion of the victim nodes. This paper proposes a security integration between 6LoWPAN and the Routing Protocol for Low Power and Lossy Networks (RPL) through the Chained Secure Mode (CSM) framework as a possible solution. Since the CSM framework provides a mean of immediate-sender trust, through the use of Network Coding (NC), and an integration interface for the other protocols (or mechanisms) to use this trust to build security decisions, 6LoWPAN can use this integration to build a chain of-trust along the fragments routing path. A proof-of-concept implementation was done in Contiki Operating System (OS), and its security and performance were evaluated against an external adversary launching a buffer-reservation attack. The results from the evaluation showed significant mitigation of the attack with almost no increase in power consumption, which presents the great potential for such integration to secure the forwarding process at 6LoWPAN Adaptation Layer.
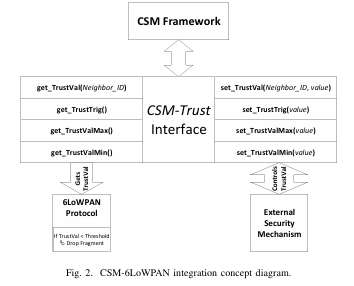
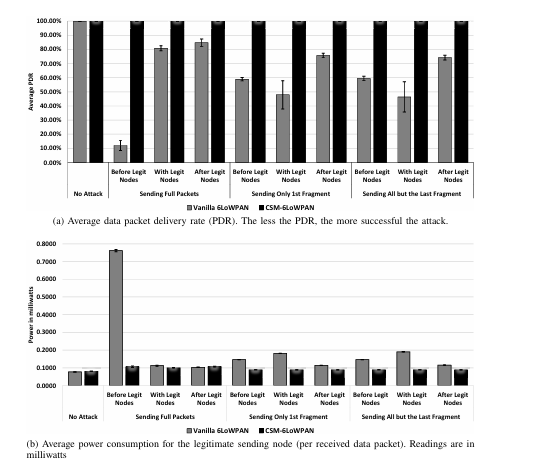
A Raoof, CH Lung, A Matrawy, “Integrating 6LoWPAN Security with RPL Using the Chained Secure Mode Framework”, The 14th IEEE International Conference on Internet of Things, 2021.
Introducing Network Coding to RPL: The Chained Secure Mode (CSM)
The current standard of Routing Protocol for Low Power and Lossy Networks (RPL) incorporates three modes of security: the Unsecured Mode (UM), Preinstalled Secure Mode (PSM), and the Authenticated Secure Mode (ASM). While the PSM and ASM are intended to protect against external routing attacks through an optional replay protection mechanism, recent research showed that RPL in PSM is still vulnerable to many routing attacks, both internal and external. In this paper, we propose a novel secure mode for RPL, the Chained Secure Mode (CSM), based on the concept of intra-flow Network Coding. The main goal of CSM is to enhance RPL’s resilience against replay attacks, with the ability to mitigate some of them. The security and performance of a proof-of-concept prototype of CSM were evaluated and compared against RPL in UM and PSM (with and without the optional replay protection) in the presence of Neighbor attack as an example. It showed that CSM has better performance and more robustness and efficiency compared to both the UM and PSM with the replay protection. On the other hand, it showed a need for a proper recovery mechanism for the case of losing a control message.
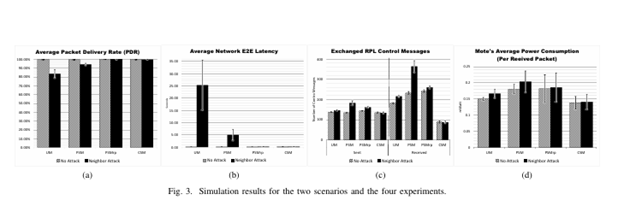
Raoof, C. -H. Lung and A. Matrawy, “Introducing Network Coding to RPL: The Chained Secure Mode (CSM),” 2020 IEEE 19th International Symposium on Network Computing and Applications (NCA), 2020, pp. 1-4, doi: 10.1109/NCA51143.2020.9306744. January 2021
Secure Routing in IoT: Evaluation of RPL’s Secure Mode under Attacks
As the Routing Protocol for Low Power and Lossy Networks (RPL) became the standard for routing in the Internet of Things (IoT) networks, many researchers had investigated the security aspects of this protocol. However, no work (to the best of our knowledge) has investigated the use of the security mechanisms included in the protocol’s standard, due to the fact that there was no implementation for these features in any IoT operating system yet. A partial implementation of RPL’s security mechanisms was presented recently for Contiki operating system (by Perazzo et al.), which provided us with the opportunity to examine RPL’s security mechanisms. In this paper, we investigate the effects and challenges of using RPL’s security mechanisms under common routing attacks. First, a comparison of RPL’s performance, with and without its security mechanisms, under three routing attacks (Blackhole, Selective-Forward, and Neighbor attacks) is conducted using several metrics (e.g., average data packet delivery rate, average data packet delay, average power consumption… etc.) Based on the observations from this comparison, we come up with few suggestions that could reduce the effects of such attacks, without having added security mechanisms for RPL.
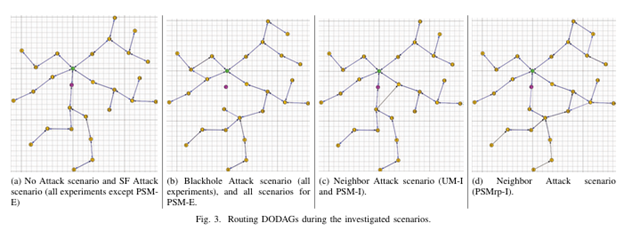
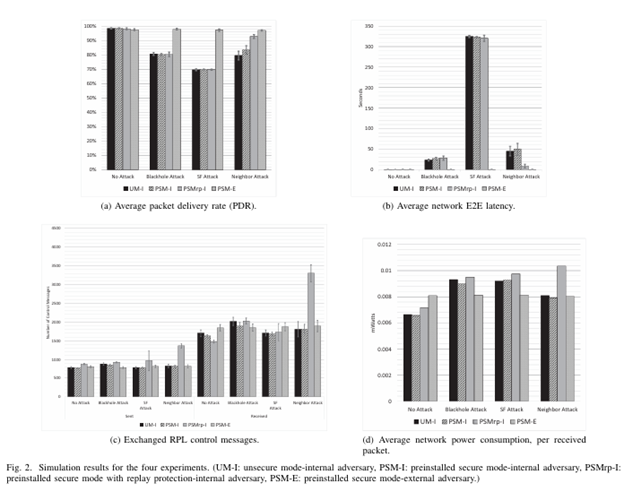
Ahmed Raoof, Ashraf Matrawy and Chung-Horng Lung, “Secure Routing in IoT: Evaluation of RPL’s Secure Mode under Attacks”, in Proc. of the IEEE Global Communications Conference (GLOBECOM 2019), Waikoloa, HI, USA, 9 – 13 December 2019.