We study the security of 5G mobile networks and securing 5G using slice isolation. Following are our recent projects on 5G security:
Security Analysis of Critical 5G Interfaces
In this work, we investigate the interfaces-specific security recommendations presented by most active Standardization Development Organizations (SDOs), analyze the potential security gaps, characterize threats caused by such gaps, and categorize those threats according to the Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege (STRIDE) model. To the best of our knowledge, our work is the first to conduct a 5G security analysis from the perspective of network architecture.
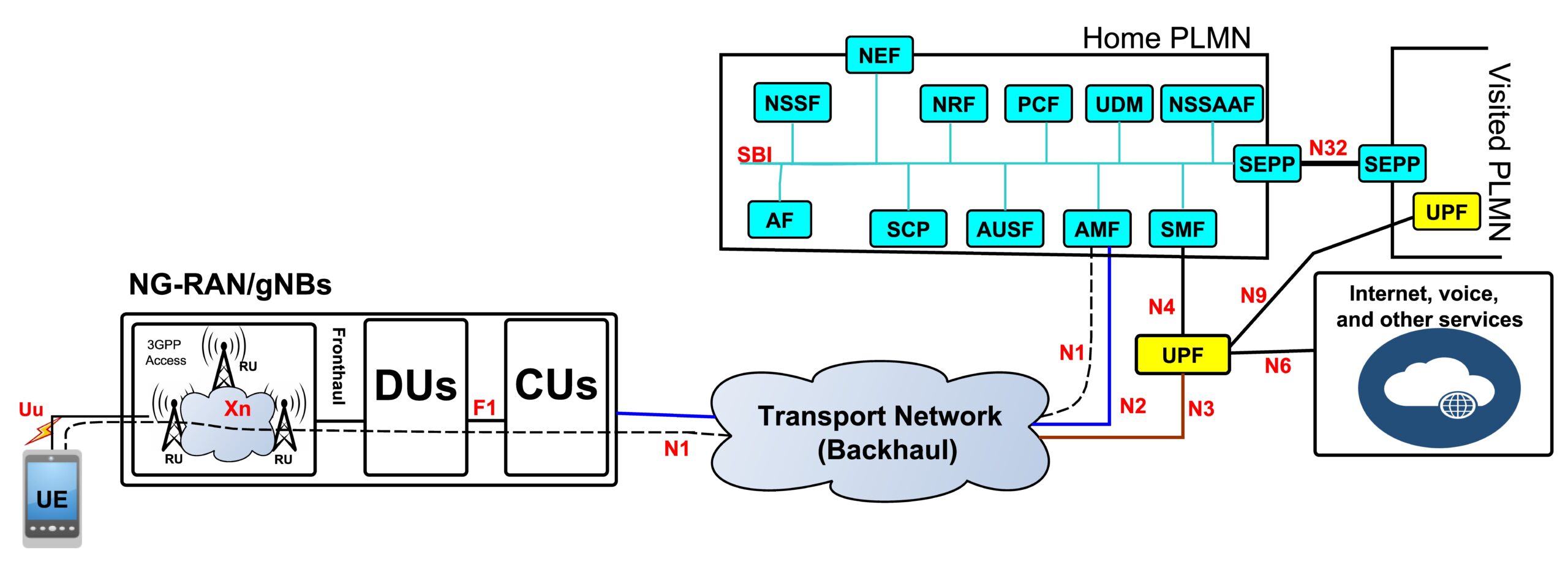
[1] Mahyoub, M., AbdulGhaffar, A., Alalade, E., Ndubisi, E. and Matrawy, A., 2024. Security Analysis of Critical 5G Interfaces. IEEE Communications Surveys & Tutorials.
A STRIDE Threat Model for 5G Core Slicing
In this research, we use the STRIDE threat modeling methodology to analyze risks associated with 5G slicing. We focus solely on the advent of network slicing, which is the ability to allocate a virtual “slice” of the network to a client and optimize the features of the slice to the specific needs of the client without impacting other slices. Our threat model is exclusively concerned with identifying threats to 5G slicing and supporting network infrastructure. Threats from previous cellular generations are also included if they are specifically a threat to 5G slicing.

[2] Sattar, D., Vasoukolaei, A.H., Crysdale, P. and Matrawy, A., 2021, October. A Stride Threat Model for 5G Core Slicing. In 2021 IEEE 4th 5G World Forum (5GWF) (pp. 247-252). IEEE.
A Security-aware Network Function Sharing Model for 5G Slicing
Sharing Virtualized Network Functions (VNFs) among different slices in the 5G is a potential strategy to simplify the system implementation and utilize 5G resources efficiently. In this research, we propose a security-aware VNF-sharing model for 5G networks. The proposed optimization model satisfies the service requirements of various slices, enhances slice security by isolating their critical VNFs, and enhances resource utilization of the underlying physical infrastructure. The model tries to systematically decide on sharing a particular VNF based on the novel security constraints that we propose in this work; the maximum traffic allowed to be processed by the VNF and the exposure of the VNF to procedures sourced via untrusted users or access networks. This sharing problem is formalized to allow for procedure-level modeling that satisfies the requirements of slice requests in 5G systems. The model is tested using standard VNFs and procedures of the 5G system rather than generic ones. The numerical results of the model show the benefits and costs of applying the security constraints along with the network performance in terms of different metrics.
[3] Mahyoub, M., AbdulGhaffar, A., Alalade, E. and Matrawy, A., 2023. A Security-aware Network Function Sharing Model for 5G Slicing. arXiv preprint arXiv:2303.03492.
On the Impact of Flooding Attacks on 5G Slicing with Different VNF Sharing Configurations
The key motivation for this work is to study the impact of flooding attacks on the performance of 5G slices with different VNF sharing configurations. We consider two VNF sharing configurations, in the first configuration, the Session Management Function (SMF) and User Plane Function (UPF) are shared among the deployed slices, while the SMF and UPF of the slices are isolated in the second configuration. The performance of these configurations is evaluated using different traffic types under two flooding attack scenarios; a ping flood attack targeting the data plane of the 5G network, and a registration request flood attack directed at the control plane of the 5G network. Our results showed different responses in the control and data planes. In the data plane, isolating VNFs of the slices provides better performance and mitigates the adverse effects of the attacks studied.
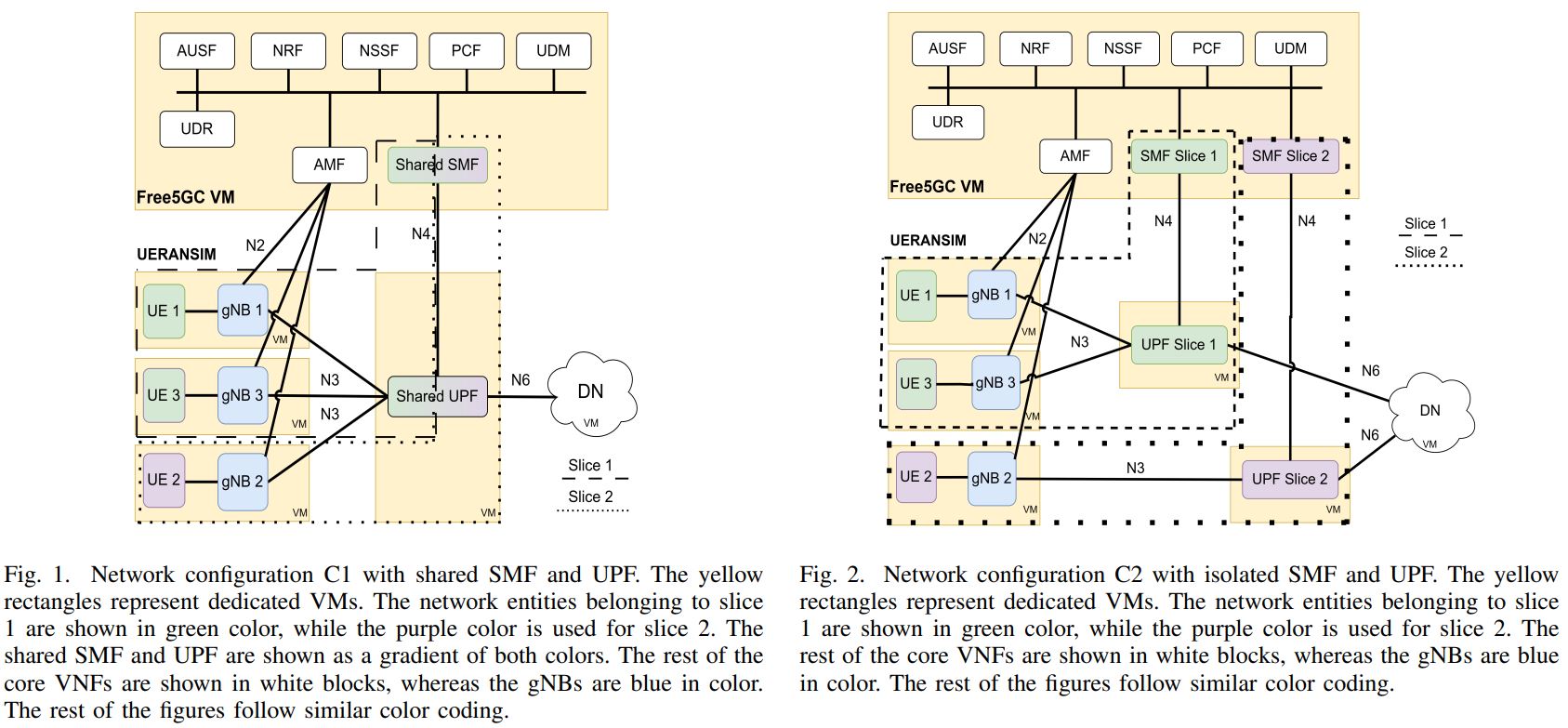
[4] AbdulGhaffar, A., Mahyoub, M. and Matrawy, A., 2024, May. On the Impact of Flooding Attacks on 5G Slicing with Different VNF Sharing Configurations. In 2024 20th International Conference on the Design of Reliable Communication Networks (DRCN) (pp. 136-142). IEEE.
A Study of XR Traffic Characteristics Under Flooding Attacks on 5G Slicing
In this research, we examine the characteristics of Extended Reality (XR) traffic across several 5G slicing configurations in the presence of attacks, including ping flood, User Datagram Protocol (UDP) flood, and registration flood attacks. The primary contribution of our research is the analysis of the impact of these different attacks on the XR traffic using different slice configurations. The results indicate the effects of the different attacks on XR traffic in terms of reducing the traffic throughput (Mbps) and the changes in the XR traffic characteristics in the different slice configurations. Also, the isolation of the Virtual Network Functions (VNFs) in the user plane provides better performance in the presence of these attacks.
[5] Husseinat, A.A., AbdulGhaffar, A. and Matrawy, A., 2024. A Study of XR Traffic Characteristics Under Flooding Attacks on 5G Slicing. Authorea Preprints.