- What is LTI
- Setting Up LTI
- Examples
- What are the Concerns
- Suggested Implementation
- Current Work
- General Resources
- LTI Tool Requests for cuLearn at Carleton University
- LTI Tool Vetting at Carleton University
What is LTI
Learning Tools Interoperability (LTI) is a technical standard or process created by the IMS Global Learning Consortium for integrating third-party applications (or “tools”) into Learning Management Systems and other educational platforms. LTI enables seamless “plug-and-play” integration of external educational applications into the University’s systems. With LTI, instructors can use collaboration and learning tools within a cuLearn course that are not part of the standard cuLearn tools. LTI handles credential exchange and management, so there is no separate student login and account creation. Instructors also have better visibility, management and reporting of student tool use. This seamless integration allows instructors to choose the best tools for their subject matter and teaching approach without having to rely on the University to add the functionality to the LMS.
Setting Up LTI
Either the instructor, with the help of the EDC, or the EDC can add a third-party tool or application to a course in cuLearn as an “External Tool” activity (currently hidden from users) using the following information in the settings provided by the Learning Tool vendor:
- Launch URL
- Consumer key and secret
The tool may be added as a link or embedded into the cuLearn interface. The following Privacy options are set depending on the level of integration needed by the tool:
- Share launcher’s name (Student’s name)
- Share launcher’s email (Student’s email)
- Accept grades from the tool
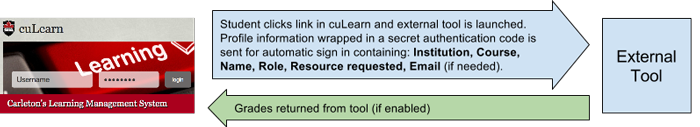
When a user is logged into cuLearn they can connect to the other tool and be automatically authenticated providing a seamless experience and without the need to set up a user account on the new system. Data can also be passed back to the cuLearn gradebook if enabled. 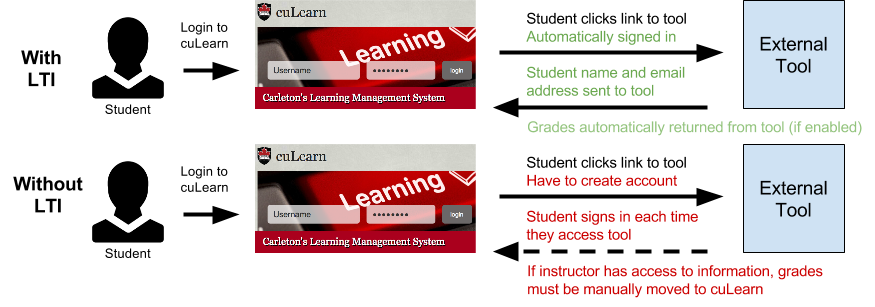
Examples
The most common use of LTI is to integrate learning tools into the campus LMS. Some examples: eduappcenter.com, piazza.com, Pearson, Wiley Plus, Mcgraw Hill, etc.
What are the Concerns
- FIPPA/Privacy – What personal information does the LTI integration expose/share in different configurations?
- Level of Integration – What kinds of information are minimally required to use an integrated LTI service?
- Data Security – retention, transfer, ownership, protection, backup
- Copyright/ownership of content and how content may be used by the vendor
- Cost of service
Suggested Implementation
Because of the privacy concerns involved with integrating third-party tools, Carleton University has developed a process for implementing third-party tools to ensure the privacy and security of our students.
- Tool Discovery – Instructor identifies tool that they wish to add to the LMS
- Vetting Process – Instructors have to apply to use LTI tools in their course. Instructor or vendor provides information on privacy, security and integration.
- Tool Added to Course – Either EDC adds integration or allows Instructor to add integration on a course by course basis.
Current Work
Recommendations and information on the following are coming:
- An outline of the implementation and vetting process
- Security and Privacy Assessment – terms of use and Compliance Certification (FIPPA)
- Data Management – what kinds of information are minimally required to use this service
- Length of term service will be available and potential tool downtime
- A list of pre-approved tool vendors
- Comparison of procedures with other Ontario and Canadian Universities
General Resources
- IMS Global Learning Consortium http://www.imsglobal.org/toolsinteroperability2.cfm
- IMS LTI Video – https://www.youtube.com/embed/R-SCdBaF-WY
- EDU Apps – https://www.eduappcenter.com/
- EDUCAUSE http://www.educause.edu/library/resources/7-things-you-should-know-about-lti
- Moodle Docs on LTI – https://docs.moodle.org/28/en/External_tool_settings
LTI Tool Requests for cuLearn at Carleton University
Communication to instructors: Please use this form to request any LTI tools to be integrated into cuLearn. Any questions or comments about this form can be sent to edc@carleton.ca * Required
- Please provide your name, school affiliation, and a contact email address.*
- Please provide the name and website for the tool you are interested in.*
- What is the primary function of this tool and why would you like to request it?*
- What course and semester are you interested in using this tool for?* (Ex: HIST 001, Intro to History, Spring 2015)
- Please provide a link to the Terms of Service for this tool, if available online. If not, write N/A.*
- Please provide a link to the Privacy Policy for this tool, if available online. If not, write N/A*
- Have you corresponded with any representatives from this vendor? If so, please provide their name and contact information. If not, write N/A.*
- Does this tool have an existing cuLearn integration that you know of?*
- Is there a cost for this tool that you are aware of?*
- What is the nature of the information that may be transmitted or stored by this LTI (e.g., names, banner ID, grades, assignments, etc.)?
- Please enter any additional comments or questions into the box below.
LTI Tool Vetting at Carleton University
Communication to vendors: Please email edtech@carleton.ca to request any LTI tools to be integrated into cuLearn.
Source file at UPenn: http://www.upenn.edu/computing/security/cloud/spia_for_vendors.pdf .This document is intended to help guide vendor response about existing or planned security controls protecting hosted data and/or systems. Responses are used to evaluate existing security posture and whether it meets Carleton University’s current recommendations and guidelines.
- Briefly summarize the service offering, identifying the location of data being stored, the type of data being stored, transmission details (how frequently, through what mechanisms), and any aspects of the service that use subcontractors or are outsourced. Please specify if any sensitive, confidential, or other protected data is planned to be stored.
- Do you have a third party security assessment and certification of your information security controls? How recently was the review performed? How regularly are reviews performed? Can you supply a copy?
- Do you have an established Information Security Program, including an Incident Response process? Your response should refer where applicable to the title of the employee in charge of the program, the number of employees in the program, any credentials or special skills, the organizations incident response program, any security policies or procedures.
- Do you have any certifications for any compliance frameworks such as FISMA, HIPAA, PCI, etc.? If custom application developed, describe any security frameworks (e.g. OWASP) used or formal processes (e.g., SDLC) in place.
- Please describe controls to address the threat of information being compromised by an external hacker or malicious software. Your response should refer where applicable to safeguards such as intrusion detection, anti-virus, firewalls, vulnerability scanning, penetration testing, encryption, authentication and authorization protections and policies, including those involving system hardening, such as passwords, removal of unnecessary network services, limiting of administrative access, code review, logging, employee training and other relevant safeguards.
- Please describe controls to address the threat of information being intercepted in transit by unauthorized persons. Your response should refer where applicable to safeguards such as encryption during transmission, availability and/or encryption of wireless traffic, physically securing devices in transit, network traffic segregation, and other relevant safeguards, and include descriptions of encryption protocols and algorithms used.
- Please describe controls to address the threat of information being mistakenly disclosed to unauthorized persons our response should refer where applicable to issues of awareness and training, removal of unnecessary data (electronic and paper), use of screen savers and lockouts, limiting storage of confidential data on remote devices, verification of identity of individuals requesting access, and other relevant safeguards that enforce “need to know”.
- Please describe controls to address the threat of information knowingly being misused by your workforce and contractors. Your responses should refer where applicable to issues of strong sanctions policy and practice, background checks, role-based access to information, oversight of data authorization by supervisor, terminating access to data for terminated employees and employees changing job functions, prohibition on sharing passwords, and other relevant safeguards.
- Please describe controls to address the threat of physical theft or loss of data. Your responses should refer where applicable to policies on the storage of confidential data on laptops, PDAs, USB drives and other portable devices, encryption of data on portable devices, two factor authentication, removal of unnecessary information, physical protection of desktops and servers, and other relevant safeguards.
- Please describe controls to address community concerns regarding privacy practices. Your responses should refer where applicable to privacy statements, opt-‐in or opt-‐ out consents, compliance with applicable privacy rules, and other relevant safeguards.
- Please describe controls to address the use, handling, protection and sharing of confidential data shared with subcontractors. Your responses should state any relevant relationships that may induce additional risk to the safe storage of sensitive data (such as outsourcing of key services, use of subcontractors or cloud services for hosting, etc.) and refer where applicable to contractual safeguards and reviews of security programs / practices.
- Please describe controls to address threats to the availability of data based on inadequate business continuity procedures.
- Your responses should refer to business continuity and disaster recovery plans and procedures, regular testing, routine data backups and offsite storage.