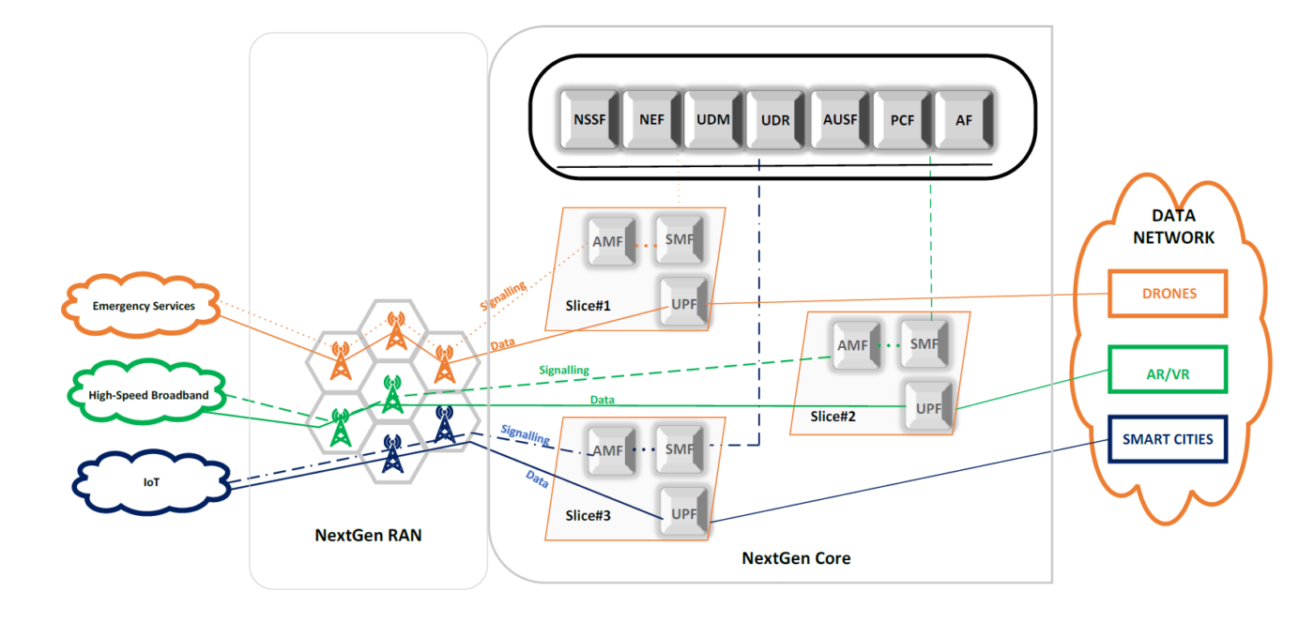
The key motivation for this work is that future smart services (e.g. IoT applications) will have competing and perhaps conflicting networking performance requirements. These services will also require flexible and agile deployment. 5G networks, an essential component of future virtualized infrastructures, deal with this issue – in part – by relying on network slicing. To define a network slice, one has to consider the allocation of recourses – both in the radio and core parts – of the 5G network to form a logical entity where a service could be deployed. Network slicing has emerged as a key-enabler for proving heterogeneous services. It takes advantage of the virtualization elements of future networking infrastructures where multiple services can be hosted on the same physical infrastructure.
A shift in the mobile network paradigm also mandates changes in the security architecture with new security challenges that do not exist in the past or present mobile networks. In the current mobile network, if an attacker launches flooding Distributed Denial of Service (DDoS) attack against a mobile service, only that service will be affected, and there is a very low risk of host resource starvation-based attacks in current mobile networks (i.e., usually mobile network infrastructure is not virtualized). However, in a 5G network, a DDoS against one slice might affect other services because they could be tenants of the same shared virtualized infrastructure. An important requirement for 5G network slicing is isolation.
Slice Allocation:
Two key challenges of 5G network slicing are function isolation (intra-slice) and guaranteeing end-to-end delay for a slice. In this work, we address the question of optimal allocation of a slice in 5G core networks by addressing these two challenges. We create a model that satisfies constraints on end-to-end delay as well as isolation between components of a slice for reliability.
[1] D. Sattar and A. Matrawy, “Optimal slice allocation in 5g core networks,” in IEEE Networking Letters, vol. 1, no. 2, pp. 48-51, June 2019.
DDoS Mitigation using Slice isolation:
In this research, we address the issue of DDoS attacks in 5G network slicing. In 5G virtualized network, multiple tenants will share the same physical resources. A DDoS attack on one slice could disrupt the services hosted on other slices. We try to mitigate the Distributed Denial-of-Service (DDoS) attacks using slice isolation (i.e., inter-slice and intra-slice isolation).
Inter-slice isolation provides mitigation against the DDoS attacks because the hardware resources are not shared between the slices and DDoS on one slice does not impact the other slices. Whereas intra-slice isolation provides better availability for the slices since the components of the slice are hosted on different hosts. Enabling intra-slice isolation could reduce the impact of DDoS attack and increase the availability of the target slice as well as faster recovery of the service because the slice operator may not need to deploy reactive mitigation defense for all slices (e.g., migrating only affected slices).
[2.] D. Sattar and A. Matrawy, “Towards Secure Slicing: Using Slice Isolation to Mitigate DDoS Attacks on 5G Core Network Slices,” to appear in 7th Annual IEEE Conference on Communications and Network Security (CNS 2019), June 2019.
DSAF: Dynamic Slice Allocation Framework for 5G Core Network:
To automate the process of slice allocation in 5G core network, we propose a framework. In the proposed framework, slices can be allocated and deallocated dynamically [3]. The Dynamic Slice Allocation Framework (DSAF) consists of five components as shown in Fig. 2.
[3.] D. Sattar and A. Matrawy, “DSAF: Dynamic Slice Allocation Framework for 5G Core Network,” CoRR, vol. abs/1905.03873, 2019.