Annually the SCS Linux Network hosts are upgraded, and the ssh-keys will no longer match. If you know that the server has been upgraded and your ssh-keys no longer match, then it will be safe to accept the new ssh key. Your system administrator will be able to confirm if this is due to a legitimate server upgrade or if it is a ‘man in the middle attack’.
- Putty Key Exchange Error
-
Putty key exchange error
The windows Putty-ssh error will look like this:
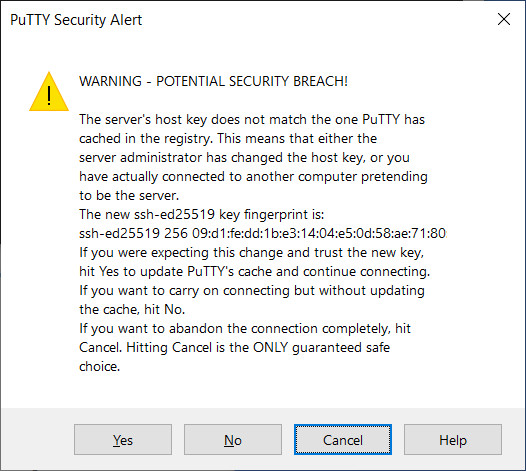
Select ‘Yes’ if you know that the host has been recently upgraded, otherwise select ‘Cancel’.
- x2g0 Key Exchange Error
-
x2go key exchange error
If you attempt to connect via x2go, the key exchange error will be as follows:

And if you wish to accept the new ssh-key, you will need to select ‘No’ and then accept the new ssh-key
Linux: Host Identification has changed ERROR
In Linux, when a host has changed, it can generate the ‘host identification error’ and the entry can be updated as follows:
ssh-keygen -R <user>@<hostname>
Where <user> is your username and <hostname> is your destination hostname.
- Host Identification Changed Error - Example
Example: Updating the host identification
Here <user> johndoe is trying to connect to <hostname> vmicron02:
First johndoe gets this error:
[johndoe@access3 ~]$ ssh vmicron02
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: POSSIBLE DNS SPOOFING DETECTED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
The ECDSA host key for vmicron02 has changed,
and the key for the corresponding IP address 134.117.xxx.xxx
is unchanged. This could either mean that
DNS SPOOFING is happening or the IP address for the host
and its host key have changed at the same time.
Offending key for IP in /home/johndoe/.ssh/known_hosts:27
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
@ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@
IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY!
Someone could be eavesdropping on you right now (man-in-the-middle attack)!
It is also possible that a host key has just been changed.
The fingerprint for the ECDSA key sent by the remote host is
SHA256:tw38tTL+JOMbEAR4Mer0ZA/gPYp4sIcXq5KWoS8n4.
Please contact your system administrator.
Add correct host key in /home/johndoe/.ssh/known_hosts to get rid of this message.
Offending RSA key in /home/johndoe/.ssh/known_hosts:15
ECDSA host key for vmicron02 has changed and you have requested strict checking.
Host key verification failed.
johndoe fixes the error by removing the hosts from the known_hosts file:
[johndoe@access3 ~]$ ssh-keygen -R vmicron02
# Host vmicron02 found: line 13
# Host vmicron02 found: line 15
/home/johndoe/.ssh/known_hosts updated.
Original contents retained as /home/johndoe/.ssh/known_hosts.old
johndoe next attempt to ssh should succeed (once they agree to add the new server to the known_hosts file):
[johndoe@access3 ~]$ ssh vmicron02
The authenticity of host 'vmicron02 (134.117.xxx.xxx)' can't be established.
ECDSA key fingerprint is SHA256:tw38tTL+JOMMEAR4Mer0ZA/gPYNp4sIcXq5KWS8n4.
ECDSA key fingerprint is MD5:a0:4:2c:43:a8:20:f:a1:d4:52:d1:52:11:e0:f5:e6.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added 'vmicron02' (ECDSA) to the list of known hosts.
johndoe@vmicron02's password:
Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-42-generic x86_64)
School of Computer Science
_____ _
/ ___ \ (_) www.scs.carleton.ca
| | | |____ _ ____ ____ ___ ____
| | | | \| |/ ___)/ ___) _ \| _ \
| |___| | | | | ( (___| | | |_| | | | |
\_____/|_|_|_|_|\____)_| \___/|_| |_|
L i n u x N e t w o r k
No matching key exchange method found ERROR
Some ssh clients may complain about: “Unable to negotiate with 134.117.xxx.xxx port 22: no matching key exchange method found.”
This is due to the destination server running an old ssh-cypher. Be aware that this may be an insecure connection as the cypher itself is no longer secure. You can try connecting as follows:
ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 access.scs.carleton.ca
You may want to contact the system administrator to inform them of the outdated ssh-server.
Tuesday, November 12, 2024 | Categories: ssh
Share: Twitter, Facebook
Short URL:
https://carleton.ca/scs/?p=16156

