- Overview
- Requirement
- Target Audience
- Purpose of Data Protection Risk Assessments
- Timing and Duration
- Data Protection Risk Assessment Process
Overview
A Data Protection Risk Assessment (DPRA) is a process involving the Service Delivery & Quality group, the Information Security group, and the Privacy Office that is used to determine the level of risk to security and privacy of data associated with the purchase and use of an IT system or service. The outcome of a DPRA is a detailed report that lists the risks associated with the IT system or service, a score identifying the risk level, and recommendation(s) to address any significant risks identified. With this report, the client is able to make informed decisions about the purchase of an IT system or service to protect the users of the system, and the university as a whole.
Requirement
The confidentiality, integrity and availability of the university’s information must be preserved when stored, processed or transmitted by a third-party cloud computing provider. Data Protection Risk Assessments are required by the university’s Data Protection Risk Assessment policy for all cloud computing services contracted by the university.
Target Audience
Data Protection Risk Assessments are for the use of faculty or staff that are involved in acquiring a new cloud-based IT system or service.
This excludes the purchase of IT systems by faculty or staff for personal use outside of the Carleton network and excludes students who may purchase an IT system or service for academic or personal reasons.
This also excludes service contracts that must be publicly tendered in a competitive bid process (RFP). Information on service contracts that require an RFP is available on Procurement Services’ How to Buy page.
Purpose of Data Protection Risk Assessments
Data Protection Risk Assessments were created to provide a rigorous and consistent means of assessing the inherent risk to data security and privacy in purchasing an IT system or service. Using industry standard protocols from EDUCAUSE and the National Institute of Standards and Technology (NIST), experts from Information Technology Services (ITS) and the Privacy Office assess potential risks and offer guidance on how to mitigate those risks. This service provides protection for the client, the users of the system or service, as well as the reputation of Carleton University.
Timing and Duration
It is extremely important that the client initiate a Data Protection Risk Assessment process before they have purchased the desired IT system or service. Waiting until after the purchase removes any opportunity for internal stakeholders to negotiate terms of purchase that will better protect the client, users, and the university.
Data Protection Risk Assessments vary widely in duration, depending upon what information is available from the client, any 3rd party security assessments and the nature of the IT system or service. They can range from a few days to several months.
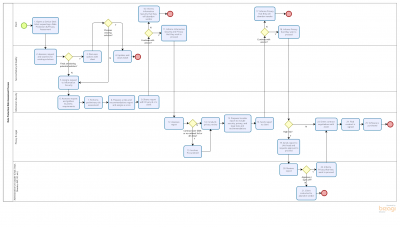
Data Protection Risk Assessment Process
The following list outlines the general steps of the DPRA process. Each assessment is tailored to the needs of the client and the nature of the IT system or service.
- The client submits a request through the ITS Service Desk for a Data Protection Risk Assessment.
- The ITS Service Delivery & Quality group looks for an existing alternate solution. If one is found and the client is willing to use it, the ticket is closed. Otherwise, the service request is assigned to ITS Information Security.
- If Information Security is assigned, they perform a security assessment and create a report that is sent to the client identifying the risks associated with the IT system or service, recommendations to mitigate the risk, and a risk score to indicate the level of risk.
- The client must decide whether to continue with the vendor. If they choose to continue, the Privacy Office is assigned. If they choose not to continue, the ticket is closed.
- If the Privacy Office is assigned, they perform a privacy assessment, and create a broader report to include data protection and legal risks mitigations. At this point, you should send any contractual documentation to the Privacy Office if you have not already done so, and the contract review is necessary for the final report. This report is then sent to the client.
- The client must again decide whether to continue with the vendor. In cases where high risks are indicated, sign-off from the head of the department or unit may be requested. If the client chooses to continue, contract negotiations take place between the university and the vendor to mitigate risk.
- Once contract negotiations are completed, the contract is signed, and the client may purchase and implement the IT system or service. A copy of the signed contract should be sent to Legal Services for recordkeeping purposes.
A process flowchart is also available: